Application Security is really hard. It runs broad, covering topics ranging from security requirements to automated misuse and abuse test cases based on a systematic threat modeling. It runs deep, as most practices require a monumental amount of knowledge. AppSec is also a moving target. Topics like supply chain risk management and AI have fundamentally shifted the threat landscape we are currently facing. On this page, I share insights drawn from my unique experience as a security researcher, industry practitioner, and OWASP SAMM core team member.
Resources and learning materials
Podcasts
Frameworks and maturity models explained
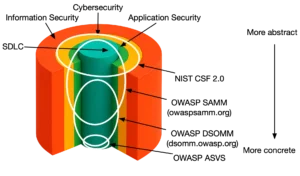
ISO 27001, NIST CSF, OWASP SAMM … What are all these things called frameworks? Aren’t they only relevant for the GRC teams in very large organizations?
This episode of AppSec Science provides a comprehensive overview of what frameworks are and their added value for systematically managing risk across teams, business units and entire organizations. I map out the full domain of application security, from the broad world of information security all the way down to the most scoped domain, the software development lifecycle.
The realities of application security risk management with CVEs and CVSS scores
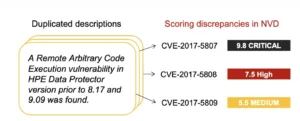
Many organizations manage their application security risk with Common Vulnerability Enumerations, or CVEs, with their impact CVSS scores. This set of resources unpacks various issues related to CVEs and CVSS scores. CVEs are like democracy, the best system available, so I provide key insights into how to use them effectively.
Security metrics with purpose and strategic impact
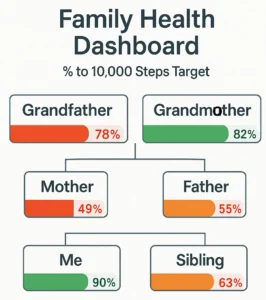
“If you cannot measure it, you cannot improve it”. However, if your security strategy is built on questionable metrics, you might not be improving the right things. These resources challenge industry assumptions and provide scientific backing to the fact that many widely used security metrics in the industry might be vanity numbers.
Security requirements driven development
Creating software is all about translating requirements into an executable piece of code. Defects are deviations from those requirements and expectations. Security requirements are a particular type of requirements that specify expectations regarding confidentiality, integrity and availability properties. Vulnerabilities are deviations from those expectations. Hence, in its extreme – no security requirements, no vulnerabilities!
![]() Watch on Youtube
Watch on Youtube
Selected blogs
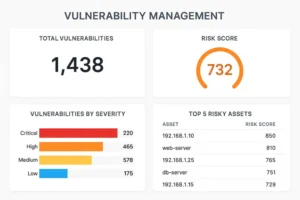
Top Application Security Failures in Fortune 500 Companies
For many organizations it’s their proverbial January 1st when it comes to their security. They’ve decided it’s time to get serious about security. They want to move beyond checkbox compliance and toward real maturity. hey allocate budget, adopt frameworks like OWASP SAMM or DSOMM.
In this article, I’ll walk you through the 6 most common AppSec failures I’ve seen across many teams and more importantly, how to avoid them. The blog is based on insights from 40+ SAMM Assessments as well as a follow-up improvement track I’ve been involved in.
Read about key pitfalls when implementing an AppSec program in Fortune 500 companies and beyond.
Free on-demand trainings

Building effective security metrics course
Many security metrics used throughout the industry are vanity numbers. Science says that they are nothing but noise. In this completely 100% free course, I provide a systematic framework and a set of tools that can help you set up a sound metrics program in your organization.

OWASP SAMM fundamentals course
In this completely 100% free course, as part of the SAMM core team I provide an overview of the OWASP Software Assurance Maturity Model. I dive deep into its five Business Functions and provide guidance when it comes to the nitty gritty of each Security Practice.
The course has received a lot of great reviews and has an average rating of 5.
Enroll free now and learn all about a world class and industry standard application security program.