Updated: 18 January, 2024
26 April, 2023
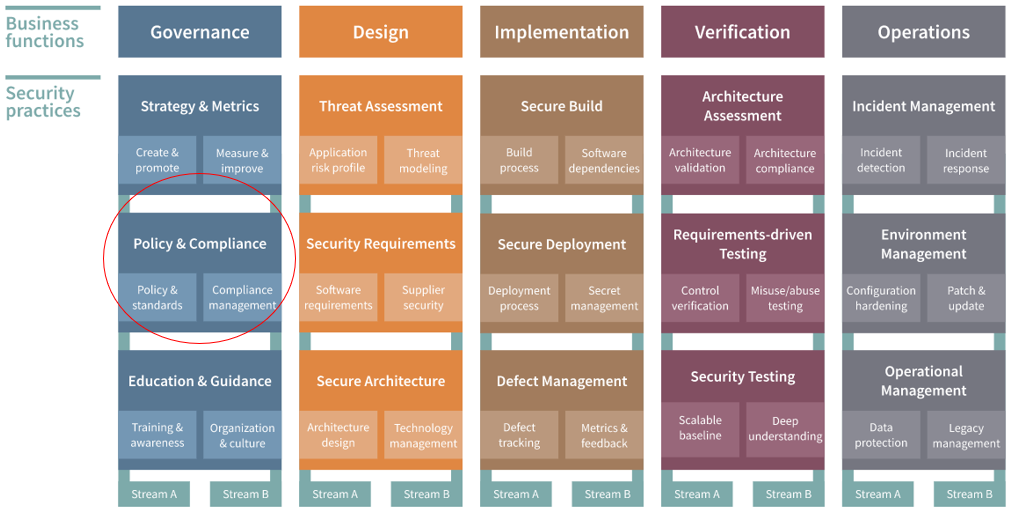
OWASP is the Open Worldwide Application Security Project. It is a non-profit foundation that works to improve the security of software. One of its most recognized contributions to the field of application security (AppSec) is the Software Assurance Maturity Model (SAMM). SAMM is an AppSec programme that provides organizations an effective and measurable way to analyze and improve their secure software development lifecycle (SSDLC). This model is divided into five business functions, each of which are subdivided into three security practices. In this blog post we will focus on the OWASP SAMM Policy and Compliance practice of the Governance business function, what it is and how you can evaluate and improve your security posture in this practice, using our management tool, SAMMY.
Most importantly, we will include insights from the OWASP SAMM Fundamentals Course which is taught by Aram Hovsepyan. He is the CEO of Codific, an expert in data security and privacy, and an OWASP SAMM Core team member.
We have also written several blogs about other practices in the SAMM framework like Stress Testing, Education and Guidance, Security Architecture, Threat Modeling and Secure Build. We will continue to write articles about the different practices so make sure to stay tuned for that.
Key takeaways
- Aligning your organization’s internal security policies with external legal and regulatory requirements can be a game changer in maintaining compliance and security.
- It is important to create technology-neutral security standards that are not only robust but adaptable to various technologies, enhancing overall security.
- Integrating legal and regulatory requirements into your organization’s security practices, ensuring full compliance while maintaining operational efficiency, can be an intricate but most often necessary process.
- SAMMY serves as a pivotal tool in managing and optimizing your organization’s security posture in alignment with the SAMM framework.
- Evaluating and continuously improving your security practices leads to a more resilient and secure organizational environment.
What is the Policy & Compliance practice of the OWASP SAMM framework?
The video below gives a brief introduction to the Policy & Compliance practice of the Governance business function in SAMM:
As explained, the main purpose of this practice is to understand and meet external legal and regulatory requirements through establishing internal security standards. The main avenue through which this is done is by describing organization’s standards and obligations with third parties as application requirements. This way automated audits can be leveraged to demonstrate the expectations are met. Moreover, this practice also focuses on ensuring that across the organization there is a shared understanding of the internal standards and external compliance requirements.
Definitions
To properly understand the practice, there are three definitions that you need to understand:
- Policy: This is a formal statement that states the organizational objectives, the roles and responsibilities required to meet them and why does the organization have them.
- Standard: This is a statement depicting the actions needed to support the policy objectives.
- Procedure: The approved ways of achieving the objectives. Furthermore, a process is usually a relationship between several procedures for how we get something done across the organization.
The two streams of the Policy & Compliance practice
The two streams of the Policy & Compliance practice are “Policy & Standards” and “Compliance Management”. As all streams in the SAMM model, each of these consist of four maturity levels (level 0 being tacit) that indicate the extent to which your organization meets the assessment criteria and coverage that the SAMM model proposes. The video below explains what the maturity levels mean in SAMM, for all practices:
Stream A – Policy and Standards
The Policy and Standards stream of the Governance function in OWASP SAMM is integral for ensuring consistent, technology-agnostic policies and standards that align with compliance requirements. The establishment of these policies, vital for application security practices like code reviews and automated security testing, happens without tying them to specific technologies or protocols. The stream undergoes evaluation across three maturity levels.
Maturity Level 1
This level checks if the organization has a common set of policies and standards, and if project teams are aware and align their practices with them. Some practical points to consider when aiming to achieve this maturity level include:
- Policies should focus on high-level definitions and broader objectives of protecting computing environment integrity, data safety and privacy, and improving software development life-cycle maturity.
- Standards should incorporate policy requirements and provide technology-specific implementation guidance.
- Expert input from senior developers and architects should be used in creating and periodically updating standards in a format that enables maintenance and audits.
Maturity Level 2
The focus here is on making policy checks easy for development teams, with test scripts aligned to policies for different technologies. To achieve this maturity level you can consider the following:
- Labeling and linking documents to policies and standards for ongoing updates and maintenance.
- Test scripts reinforce application security requirements, guide testing efforts, and ensure ongoing compliance as applications evolve.
- Requirements should be written in a format consistent with existing requirements management processes, and create multiple versions for different development methodologies or technologies.
Maturity Level 3
This involves assessing compliance at the project level, generating compliance reports, and using feedback to improve policies and training. Some points to consider include:
- Whenever possible, integrate compliance status into automated testing and report it with each version, including the version of policies and standards and appropriate code coverage factors.
- Encourage non-compliant teams to review available resources such as security requirements and test scripts and forward issues resulting from insufficient guidance to the responsible teams for future releases.
- Escalate issues that cannot meet policies and standards to teams that handle application security risks.
The objective is to ensure that security policies are well-integrated and effectively applied within the organizational framework, enhancing the security posture overall. The video below explains this stream further:
Stream B – Compliance Management
The Compliance Management stream of the OWASP SAMM framework’s Policy & Compliance practice focuses on meeting legal and regulatory requirements by establishing internal security standards. It plays a key role in defining the organization’s standards and third-party obligations as application requirements, which allows for conducting automated audits to demonstrate compliance. Additionally, it emphasizes the importance of a shared understanding across the organization of both internal standards and external compliance requirements.
Maturity Level 1
This level focuses on creating a comprehensive list of all compliance requirements and evaluating them with experts. Some aspects to consider are the following:
- Review each obligation with experts and legal to ensure understanding, and indicate opportunities to lower compliance burdens by changing how data is handled.
- Consider publishing a compliance matrix to identify which compliance requirements are applicable at the organizational level, and map compliance requirements to existing policies and standards.
- Update policies and standards to include organization-wide compliance requirements, and create compliance-specific standards for individual requirements.
Maturity Level 2
This level involves developing a library of application requirements and test scripts to establish and verify regulatory compliance, including re-assessing each application’s compliance requirements periodically. Consider the following points when aiming for this maturity level:
- Create a library of application requirements and test scripts that are available to all development teams. The library should address individual compliance requirements like PCI or GDPR, as well as global compliance requirements such as ISO.
- Periodically re-assess each application’s compliance requirements and review all functionality to identify opportunities to reduce scope and overall compliance costs.
- Requirements should include enough information for developers to understand the functional and non-functional requirements of the different compliance obligations, references to policies and standards, and explicit references to regulations.
- Test scripts should verify compliance and clarify compliance requirements for developers, making the compliance process transparent.
- Format requirements for importing into individual repositories.
Maturity Level 3
This level centers on developing a program for measuring and reporting the status of compliance across applications, leveraging automation for testing and assessing compliance, and developing standard reports and scorecards for managing compliance. When aiming for this maturity, consider the following:
- Use application requirements and test scripts to assess compliance status. QA, Internal Audit, or Information Security teams perform manual testing when fully automated testing is not possible.
- Track remediation actions and periodic updates, and review compliance remediation activities to ensure effective progress.
- Develop standard reports and compliance scorecards to help teams and organizations manage compliance gaps.
- Review compliance gaps requiring significant expenses or development with subject-matter experts and compare costs against minimizing scope or eliminating compliance requirements.
- Long-term compliance gaps require formal compliance risk acceptance and management approval.
This stream is pivotal in maintaining compliance with external requirements and integrating them into the organization’s security framework. The video below explains this stream further:
How can you use SAMMY to implement the OWASP SAMM Policy and Compliance practice into your SSDLC?
SAMMY is a tool that allows you to manage your organization’s security posture following the SAMM framework. It allows you to manage all practices in the model. This section focuses on how you can use it to evaluate and improve your maturity level for the Policy and Compliance practice. For this, we will explain how to implement this process in the Policy and Standards stream. The process remains consistent across the Compliance Management and other streams in various business functions, with differences mainly in the evaluation phase questions.
Usually, SAMMY users organize into teams and assign roles to each team member. The three roles that are assigned are: evaluator, validator and improver.
Evaluation
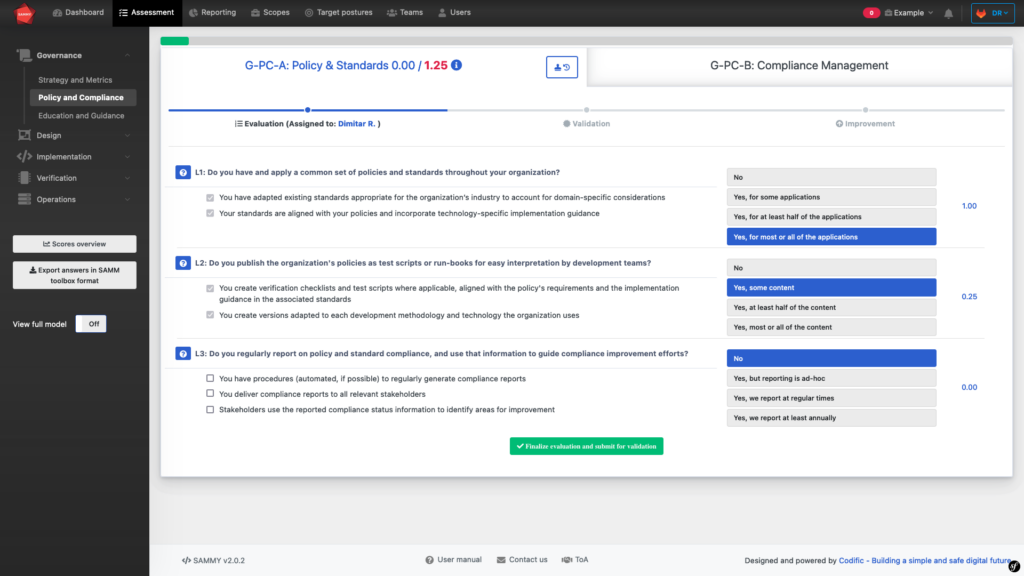
Firstly, the evaluator evaluates the security posture with regards to the Policy and Compliance practice. For these, they will answer three questions (for each stream), each of which has four possible answers, as illustrated above. Depending on what answer you choose you will score either 0, 0.25, 0.5 or 1. A score of 1 in all questions means that you have the maximum maturity level for this stream, 3. As you can see, in the example above the score for this particular stream is 1.25 out of 3.
The videos in the sections that explain streams A and B of the Policy and Compliance practice also explain how to carry out this evaluation and what to consider when doing so.
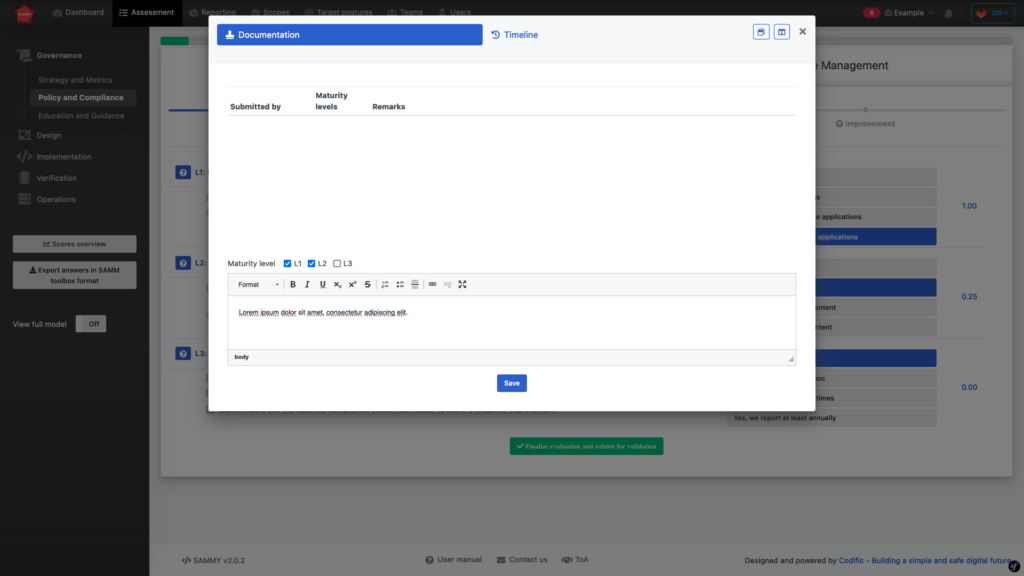
Next, the evaluator needs to present evidence to support their evaluation. This can come in the form of documentation uploaded to SAMMY or a written explanation provided in the text box above. In the next step, the validator will check this evidence to validate the evaluation.
Validation
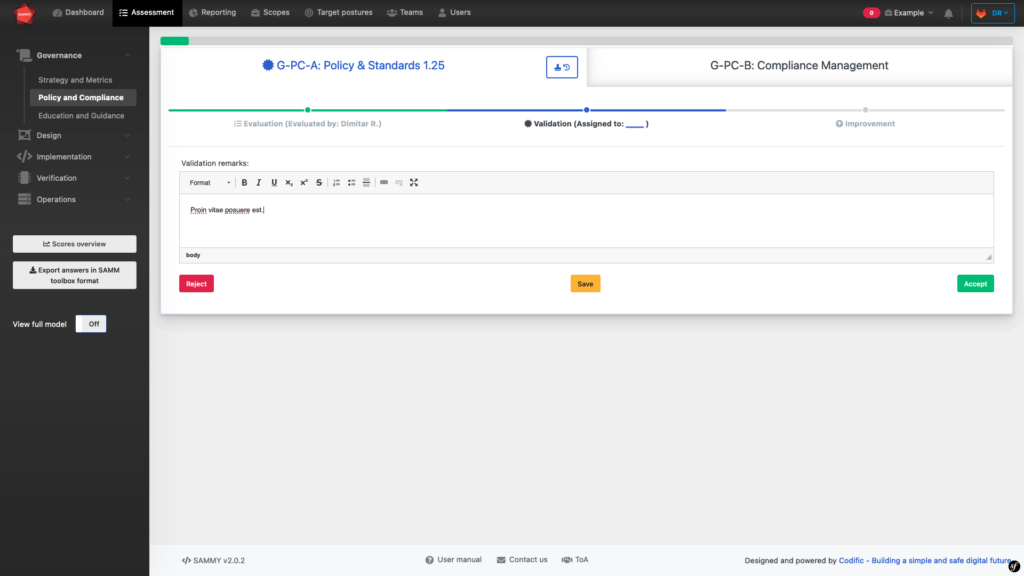
The validation step ensures correct evaluation, assigning a validator who reviews the evaluation and its supporting evidence. This validator, either an internal or external auditor, checks the company’s security posture against a specific practice. The validator accepts the evaluation if the evidence is sufficient and correct. Note that the validation step is optional at certain maturity levels. For example, at zero maturity, validation isn’t mandatory. After validation, the process moves to the third and final step: improvement.
Improvement
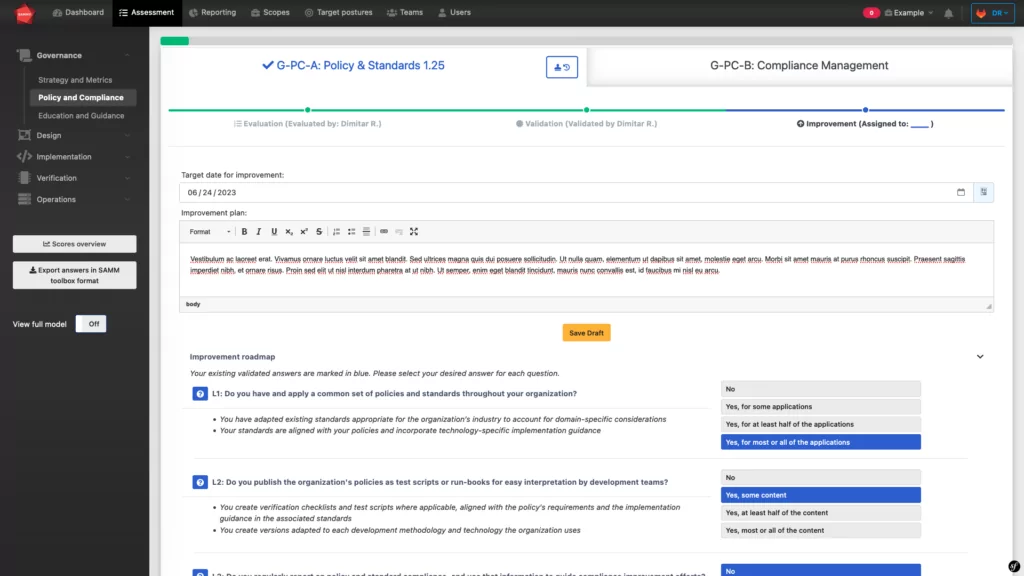
Finally, the improvement step. As shown above, this involves writing an improvement plan with a target date by which to carry out the improvement.
This step is also optional, as SAMMY was built to be used following your organization’s risk profile. Following this, your organization may not seek to improve their maturity level in a particular stream. Thus, the improvement step is not necessary.
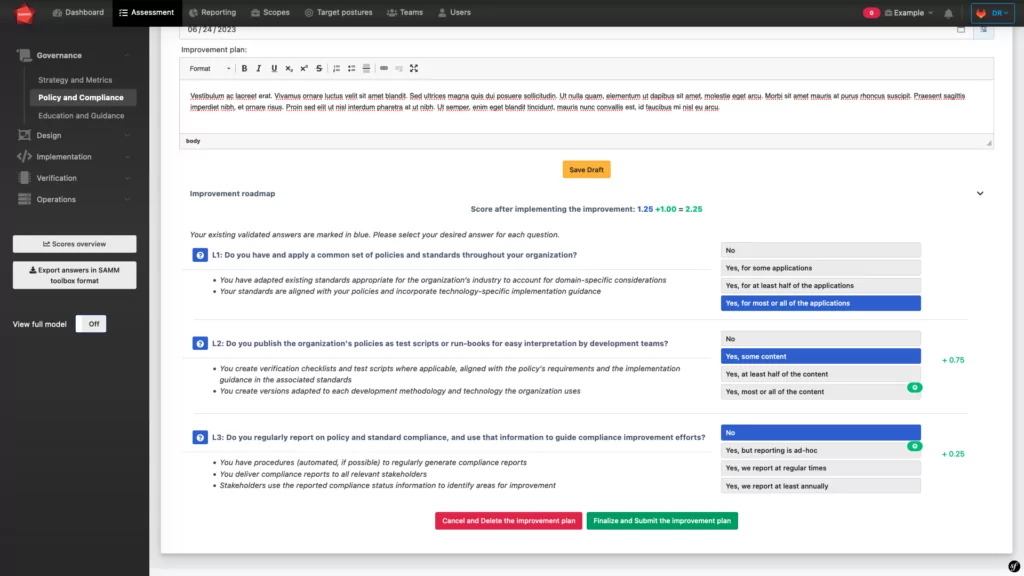
If the improvement plan is carried out, a new evaluation is done and the new maturity score is calculated.
Conclusion
In conclusion, the Policy and Compliance practice of the SAMM framework, is crucial for ensuring organizations meet security standards and comply with legal requirements. It involves structured evaluation and improvement processes across various streams. The integration of SAMMY into this practice enables organizations to efficiently evaluate, validate, and improve their security posture. SAMMY’s role-based system ensures a thorough assessment and enhancement of every aspect of the practice. Try SAMMY for free to experience how it transforms your organization’s approach to security and compliance. Moreover, if you have any question or require any guidance, then please don’t hesitate to contact us.